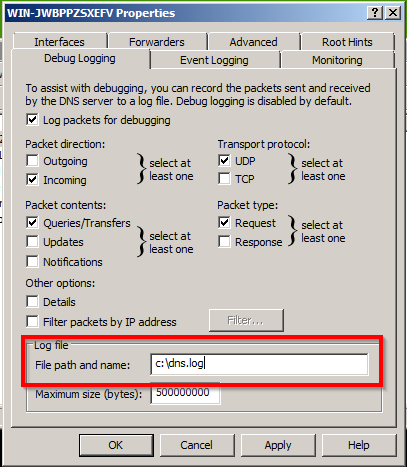
System administrators should turn on advanced debug logging from the DNS Manager console to get the most out of Windows DNS Events. Unfortunately, Microsoft did not design the debug log file for 3rd party logging and monitoring software. Administrators may encounter a DNS debug log error because of this.
A handful of Splunk and McAfee SIEM users have complained that Windows DNS logging stops after a while. Some suggest using a Scheduled Task which works because the log file is recreated every time Restart-Service DNS is run. This will resolve the DNS debug log error until the file reaches its maximum size again, but it will also restart the DNS Server service quite frequently.
Signs of the DNS Debug Log Error
- Splunk (or other monitoring software) stops logging DNS events
- An Event ID 3152 Error shows up around the same time logging stops
- The debug log file no longer exists in the set file path
- The file path for the log file is not on the same volume as the Windows OS (C:)
The Solution
Set the DNS debug log file path to a location on the same volume as the Windows OS (C); it’s that simple.
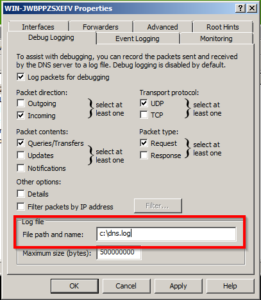
The Cause
The system backs up and deletes the log file when it reaches its maximum size, then an empty log file of the same filename is created in the same location. However, the log file is recreated in a slightly different way if it is not on the same volume as the OS. This difference is what causes the DNS debug log error that Splunk users may experience. Credit goes to adm at NXLog for finding the solution.