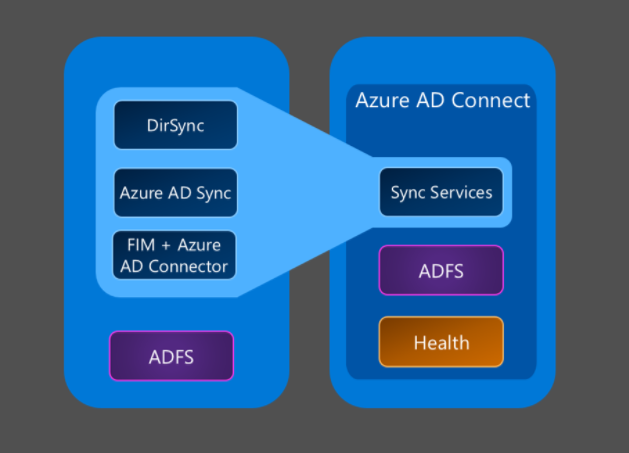
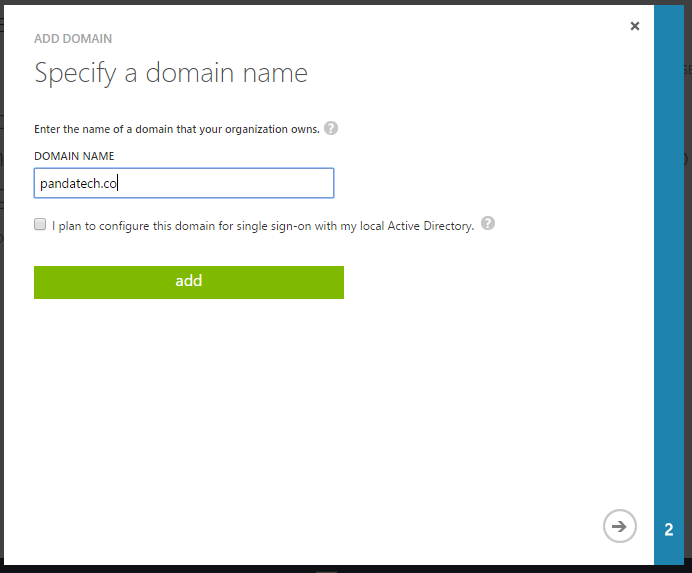
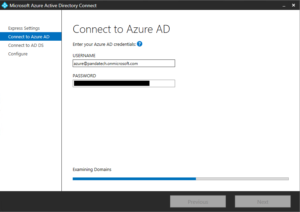
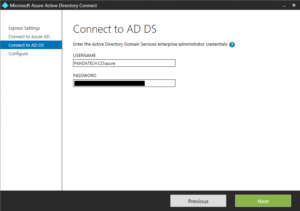
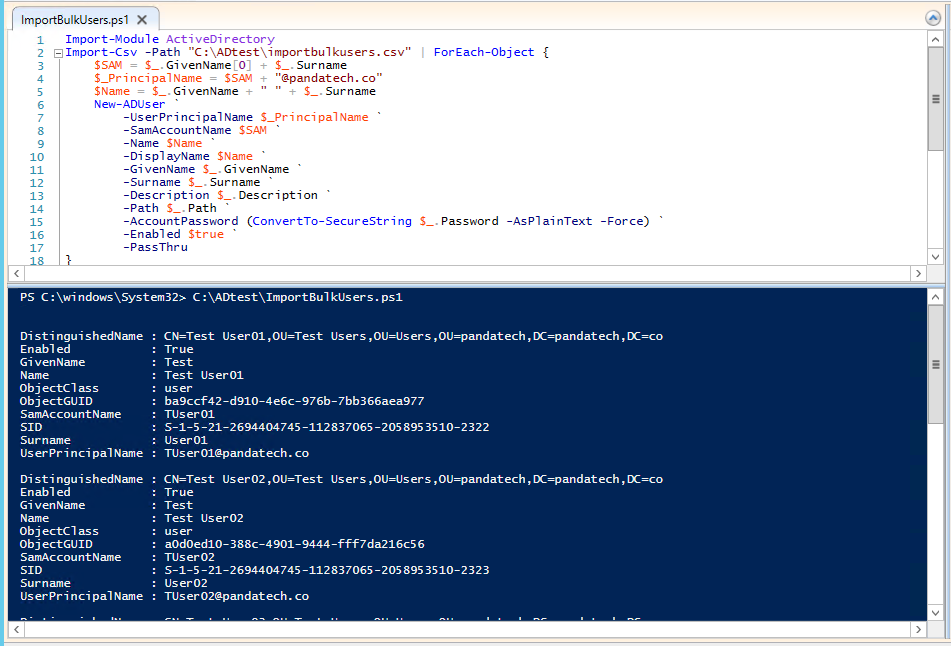
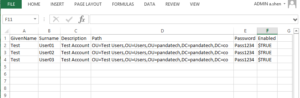
The company has moved from an on-premise Exchange Server to Office 365. You have set up AD Connect to sync all your data and passwords. You have decommissioned and uninstalled all local instances of Exchange Server. Suddenly you discover that you must manage Office 365 via Active Directory, and it seems impossible to because many settings must be changed in the Active Directory Users and Computers Attribute Editor.
Your options for management are essentially the following:
- Disable AD Connect – Your data in AD and Azure AD will no longer be synced, but you can easily manage everything from https://portal.office.com/adminportal/home#/homepage.
- Install Exchange Server locally – Your data will be in sync. You can set up Mail-Enabled Users to manage users with mailboxes, and groups and contacts will be managed the same way as before via the Exchange Management Console.
- Manage mailboxes through Active Directory Users and Computers – Your data will be in sync, and you will have the turn on “Advanced Features” to access the Attribute Editor.
This is a reference table with examples choose Option 3, and manage Office 365 via Active Directory.
| Type | Function | AD Attribute | Example |
|---|---|---|---|
| User | Hide User from Address Book | msExchHideFromAddressLists | TRUE |
| User | Set alias email | proxyAddresses | smtp:information@pandatech.co |
| User | Set primary email | proxyAddresses | SMTP:info@pandatech.co |
| User | Set Exchange Alias | mailNickname | info |
| Group | Permitted Senders | authOrig | CN=First Last,OU=IT,OU=Panda Tech,DC=pandatech,DC=co |
Frequently used Office 365 settings that are difficult to find in the AD Attribute Editor will continue to be added to the table in the future.